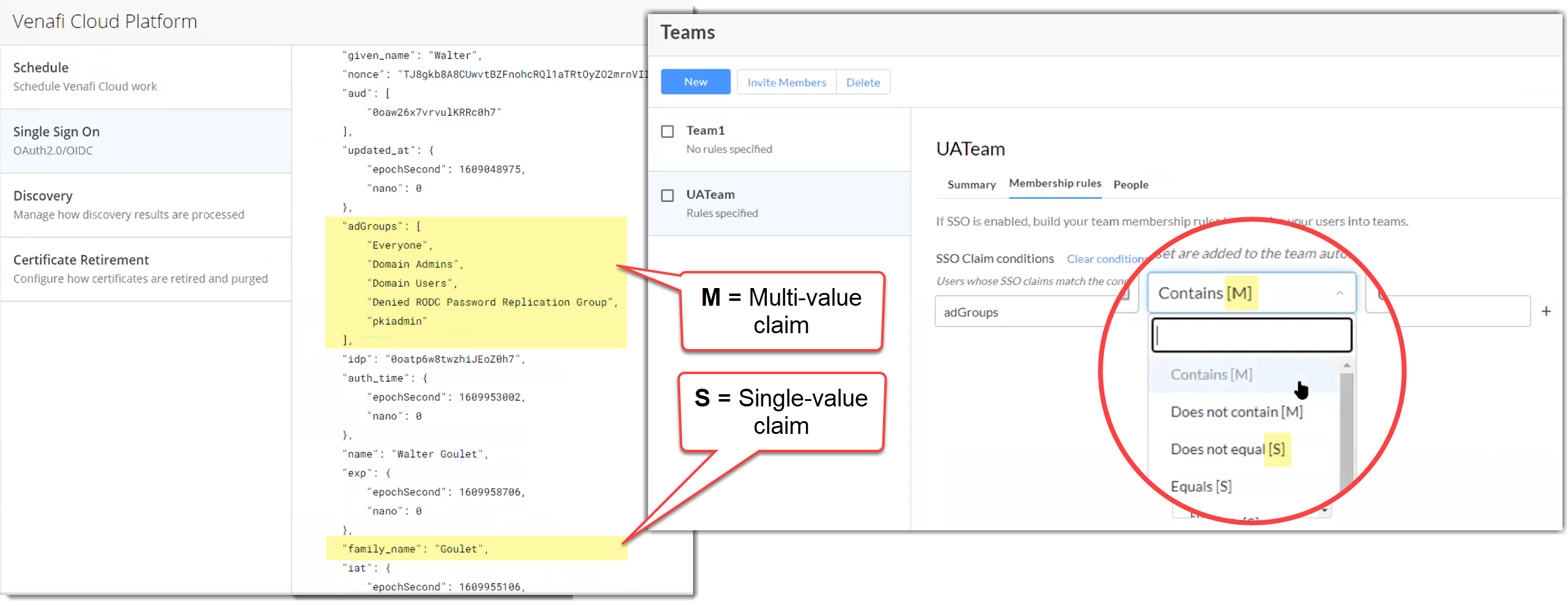
Reference: Team membership rule operators¶
TLS Protect Cloud can assign users to teams automatically using SSO group claims from your SSO provider. Users whose SSO claims match the conditions you specify in team membership rules are added to the team automatically.
Because users can be assigned to either a single group or multiple groups in a company directory, membership rule operators include values for either single [S] or multiple [M] groups. Which operator you select ([S] or [M]) when defining membership rules is important.
Before setting your member ship rules
Keep the following points in mind when creating your team membership rules:
- The values you enter in Claim name and Claim value are not treated as case-sensitive. So GroupA and groupa are treated the same.
- The Equals [S] and Contains [M] operators have the same effect. So if you specify GroupA as your claim name and configure it with either Contains [M] or Equals [S] operators, you'll get the exact same result.
For single group users [S]¶
If a user is part of a single group, then in your team membership rules, use only those operators that end with [S] (the S stands for single group).
| Single group operators [S] | Effect |
|---|---|
| Does not equal [S] | The value entered matches an SSO group and will not be added to the group. |
| Equals [S] | The value entered matches an SSO group and will be added to the group. |
| Starts with [S] | The value entered matches the beginning of the SSO group and will be added to the group. |
| Ends with[S] | The value entered matches the end of the SSO group and will be added to the group. |
For multiple group users [M]¶
If a user is assigned to multiple groups, then in your team membership rules, use only those operators that end with [M] (the M stands for multiple groups).
| Multiple group operators [M] | Effect |
|---|---|
| Contains [M] | The value entered matches the SSO group name in its entirety. For example, if a user is part of Group1, the value must be Group1 and not simply Group). If the value matches, the user is added to the group. |
| Does not contain [M] | The value entered matches the SSO group name in its entirety. If the values match, the user is NOT added to the group. |
Verifying what type of entries your SSO connection is returning¶
Test your SSO connection to see if it's returning lists multiple [M] or single entries [S]. For example, take a look at this JSON response:
The JSON returned from groups has a single entry. Notice that the brackets ([...]) indicate this is part of a list being returned, not just a single entry. So for this connection, the only valid operators are the [M] or multiple, even though in this case it's a list of only one.
How team membership rules work with SSO claims¶
SSO claims are used to identify which users should be added to your team. Users whose SSO claims match the conditions you specify in your team membership rules are added to the team automatically.
For example, suppose your organization uses Active Directory with Okta as your SSO. Your team has an AD group called GroupA that is synchronized with Okta. If Okta is configured with a Groups claim expression, the AD group named GroupA will be returned in a claim that contains the list of groups to which the user belongs. To verify your setup, sign in to TLS Protect Cloud}, go to Settings > Platform > Single Sign On, and then click Test Connection to make sure the GroupA is returned in the claim:
{
"at_hash": "yD62LRYaml6qPbZhB1aW9g",
"sub": "00uw90kf60mCkrAry0h7",
"zoneinfo": "America/Los_Angeles",
"ver": 1,
"email_verified": true,
"amr": [
"pwd"
],
...
"adGroups": [
"Everyone",
"Domain Users",
"GroupA"
],
...
}
The following diagram shows you how SSO claims map to team membership rules.
Click here to see a larger version of the image.
Learn more about SSO configuration.