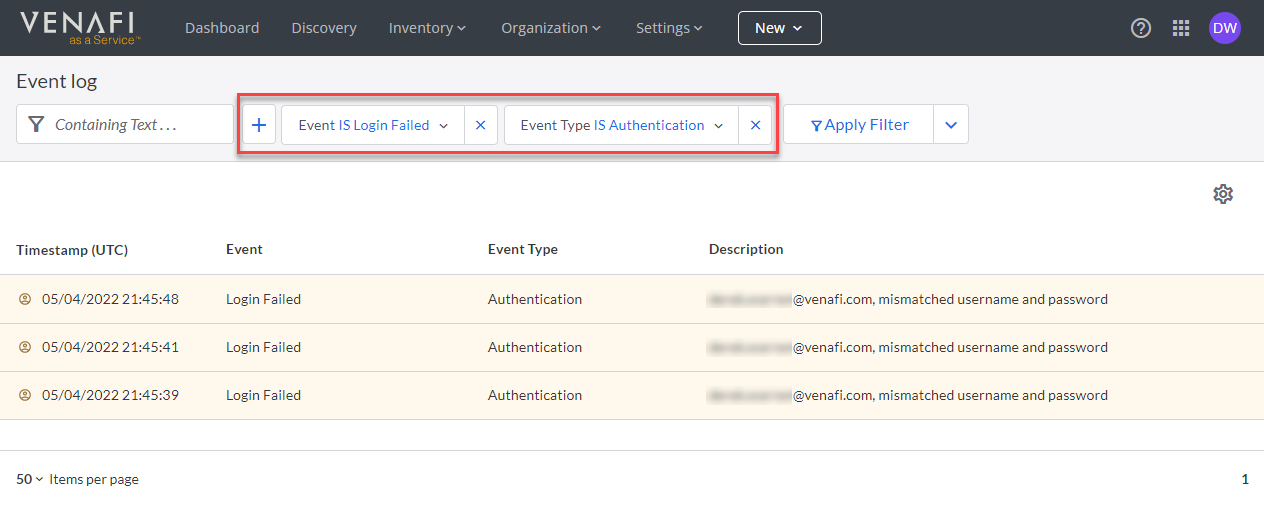
Finding logged data through filtering¶
The Event Log shows a list of all events logged as a result of either user actions or TLS Protect Cloud operational activities.
You can select and combine pre-built filters to quickly filter out logged events that don't match your filter criteria. For example, you could enter a specific user name to see all events that include that user within the event text. Or you could enter the search term login to filter the list down to only those items that include "login".
But you can also filter the list by using one or more pre-built filters.
To filter event logs using pre-built filters¶
- Sign in to Venafi Control Plane.
- Click Settings > Event Log.
- Click +, and then select one or more filters from the list.
- Click each filter's drop-down list to select one or more sub-filters.
- After you've added the filters you need, click Apply Filter.
Here's a quick reference for common tasks using pre-built filters:
| Event Log Filter Category | Criteria | Common tasks |
|---|---|---|
| Criticality | 0, 1 | Check for login failures, password changes, or if SSO is enabled. |
| Description | Free-form input | Find a user or IP address, check if a password reset is required. |
| Event | ApiKey Created | See a list of api keys created with a timestamp. |
| Event | Application Deleted | Show applications deleted and who performed the action. |
| Event | Certificate Issued | See a list of certificates issued and who the certificates were issued to. |
| Event | Certificate Retired | Show list of certificates retired. |
| Event | Certificate Validation Finished | See a list of when a certificate validation is finished, including validation status. |
| Event | Login Failed | Retrieve a list of recent login failures. |
| Event | Machine Created | See a list of machines created showing the user who performed the action, the machine's name, ID, and type. |
| Event | Machine Discovery Failed | See a list of machine discovery errors and possible causes. |
| Event | Installation Provisioning Started | See a list of machines that have started the provisioning process, showing the user who performed the action, the installation ID, the name of the certificate assigned to the installation, and the machine's name and ID. |
| Event | User Role Changed | Show user role changes, indicating new role names. |
| Event Type | App Server Types, Applications, Authentication, Certificate Authority, Certificates, Credential Management, Discovery Service Configuration, Cloud Discovery, Machine Discovery, Issuing Templates, Notifications, Platform Security, Provisioning, Teams, Trusted Certificates, User Security, User Settings, Users, VSatellite Workers, VSatellites | Search for events associated with specific event types. For example, select Provisioning to view events such as Machine Created, Machine Updated, Machine Deleted, Machine Installation Created, Machine Installation Updated, Machine Installation Deleted, Machine Installation Provisioning Started, Certificate Installed, and Machine Installation Provisioning Finished. |
| Timestamp | 7, 14, 30 days | List any events in the last 7, 14, or 30 days. |