Configure Google Cloud Platform (GCP) connection¶
The following guide illustrates connecting TLS Protect Cloud with Google Cloud Platform (GCP).
Enable TLS Protect Cloud to provision new certificates in Google Certificate Manager (GCM) for use with Google services. This guide walks you through the integration process.
Before you begin¶
You're going to need a few things to complete this procedure:
- A Google service account.
- At least one active VSatellite to provision certificates to GCP.
- Venafi permissions for GCP: You must specify these permissions when creating a service account.
Note
- Only TLS Protect Cloud-generated and user-imported certificates with private keys can be provisioned. To learn more, see Importing a private key via API (PKCS #8) and Importing a private key via API (PKCS #12).
- Only one certificate can be provisioned at a time.
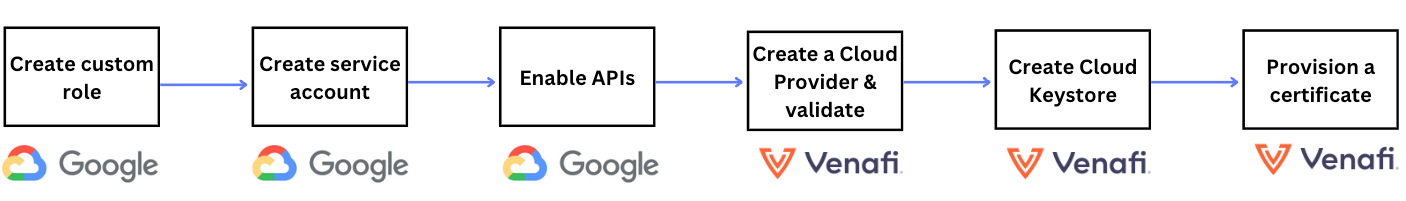
Overview¶
The following diagram illustrates the high-level steps for integrating TLS Protect Cloud with Google Cloud Platform (GCP). In the subsequent sections, we dive into each of these steps, providing you with a guided walkthrough.
Step 1: Create a Google custom role¶
You have the option to create a custom role via the console or gcloud CLI. Choose one of the below methods to create a custom role.
-
Console - See Create and manage custome roles to create a Identity and Access Management (IAM) custom role.
-
gcloud CLI - Alternatively, if you would like to use gcloud CLI to create a custom role, create the following YAML file with the included permissions.
title: TLSPC Integration
description: Permissions granted to TLSPC
stage: GA
includedPermissions:
- certificatemanager.certs.create
- certificatemanager.certs.get
- certificatemanager.certs.list
- certificatemanager.certs.update
- certificatemanager.locations.list
- certificatemanager.operations.get
- resourcemanager.projects.get
gcloud iam roles create <tlspcIntegrationRole> --project=<PROJECT_ID> --file=permissions.yaml
Use these permissions while setting up a service account:¶
| Action(s) | Required permissions |
|---|---|
| Allow TLS Protect Cloud to create (provision) a new certificate for the certificate manager. | certificatemanager.certs.create |
| Allow certificate metadata to be retrieved (after the certificate creation operation completes). | certificatemanager.certs.get |
| Verify access to the certificate manager. | certificatemanager.certs.list |
| Allow TLS Protect Cloud to replace/reprovision a certificate. | certificatemanager.certs.update |
| Allow TLS Protect Cloud to list certificate manager locations. | certificatemanager.locations.list |
| Allow TLS Protect Cloud to check an operation status (for example, certificate creation/replace). | certificatemanager.operations.get |
| To allow TLS Protect Cloud to obtain details of projects associated with the svcAccount. | resourcemanager.projects.get |
Step 2: Create a Google service account.¶
-
Follow the steps to create a Google service account at Create service accounts. This page explains how to create service accounts using the Identity and Access Management (IAM) API, the Google Cloud console, and the
gcloudcommand- line tool. -
Once complete, you will be presented with your Google service account email. Make sure to copy and save this for later use.
Note
In this step you will associate the custom role created in Step 1 with your Google service account.
Step 3: Enable Google APIs¶
In this step you will need to enable the Cloud Resource Manager API and the Certificate Manager API.
- In the Google Cloud console, go to APIs & services for your project.
- On the Library page, select Private APIs. If you don't see the API listed, that means you haven't been granted access to enable the API.
- Select the API you want to enable. If you need help finding the API, use the search field.
- In the page that displays information about the API, select Enable.
See Enabling an API in your Google Cloud project for more details.
Step 4: Create a Cloud Provider & validate the connection¶
- Sign in to Venafi Control Plane.
- Click Integrations > Cloud Providers.
- Click New and select Google.
- Enter a Name for the new cloud provider. This name will help TLS Protect Cloud users to identify this cloud provider.
- Enter your Google Service Account Email you copied from the Step 1 and click Continue.
-
Select an Owning Team. If you need to create a new team see, create a new team.
Note
- Owning Team - The Owning Team is responsible for the administration, management, and control of a designated cloud provider, with the authority to update, modify, and delete cloud provider resources.
- Authorized Team - The Authorize Team is granted permission to use specific resources of a cloud provider. Although team members can perform tasks like creating a keystore, their permissions may be limited regarding broader modifications to the provider's configuration. Unlike the Owning Team, users may not have the authority to update and delete Cloud Providers.
-
Click Create.
- In the following screen you will be presented with a Public Key, copy and paste the Public Key.
- You will now need to upload your public key for a service account. See Upload service account keys and follow the instructions.
- From TLS Protect Cloud, click the Validate button. You should see a "Successfully validated" message. If do not see this message, this means you were not able to successfully validate your connection. Go back and check your settings in the above steps.
- Click Finish. At this point, your new provider details will be displayed in the Cloud Providers list. You will also see a message that confirms you have successfully created and validated your new provider.
Step 5: Add a Cloud Keystore¶
- Sign in to Venafi Control Plane.
- Click Installations > Cloud Keystores.
- Click New and select Google.
- Enter a Name for the new cloud keystore.
- Select an Owning Team. If you need to create a new team, see create a new team.
-
Select an Authorized Team.
Note
- Owning Team - The Owning Team is responsible for the administration, management, and control of a designated cloud provider, with the authority to update, modify, and delete cloud provider resources.
- Authorized Team - The Authorize Team is granted permission to use specific resources of a cloud provider. Although team members can perform tasks like creating a keystore, their permissions may be limited regarding broader modifications to the provider's configuration. Unlike the Owning Team, users may not have the authority to update and delete Cloud Providers.
-
Select a GCP Cloud Provider.
- Enter a Project Name.
- Enter a GCM Region.
- Click Save. At this point you should see your saved new cloud keystore in the Cloud Keystore list.
Step 6: Provision a certificate¶
At this point you should now have the ability to provision certificates.
-
Click the
 button to the right of the new cloud keystore you just created and select Provision.
button to the right of the new cloud keystore you just created and select Provision.Tip
Here you also have the option to delete certificates if needed.
-
From the dropdown, search for the certificate you want, select it, and click Provision.
-
(Optional) Here, you also can re-provision, replace, or delete a certificate. These options modify an existing machine installation.
- Select your Cloud Keystore, and a details panel will appear on the right.
- Click on the
 button to the right of your certificate.
button to the right of your certificate. - Choose the appropriate action: Re-provision, Replace, or Delete, and proceed through the user interface steps until the process is complete.
Info
- Re-provision - This action re-provisions your current certificate.
- Replace - Choose this option to substitute your current certificate with a different one.
- Delete - This action removes the selected certificate from the table.
-
Go to your Google service account, under Certificate Manager, and select Certificates. Click the Refresh button. You should now see your certificate in the list with an active status.
At this point you have successfully connected TLS Protect Cloud to Google Cloud Platform (GCP) and successfully provisioned a certificate.